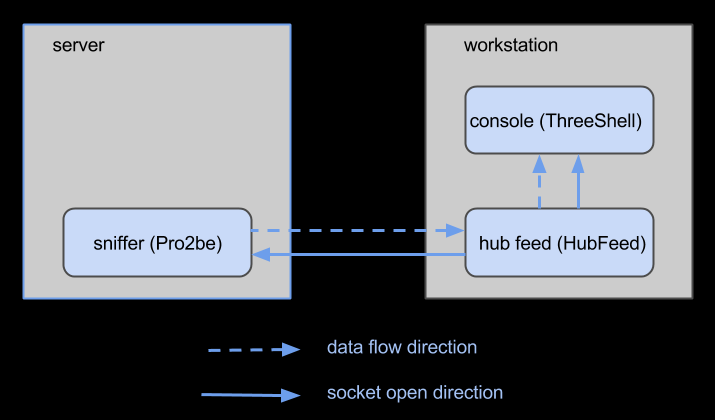
HOW TO MONITOR A SERVER USING DEEP NODE
1. Create keypairs for server and client, using the following commands:
keytool -genkey -alias server -keyalg RSA -keystore hubserver.jks -storepass deepnode
keytool -genkey -alias client -keyalg RSA -keystore hubclient.jks
keytool -export -file server.cert -keystore hubserver.jks -storepass deepnode -alias server
keytool -export -file client.cert -keystore hubclient.jks -alias client
keytool -import -file client.cert -keystore hubserver.jks -storepass deepnode -alias client
keytool -import -file server.cert -keystore hubclient.jks -alias server
You will be prompted for a password for the client keystore. The password for the server keystore must be "deepnode". Make the key passwords the same as the keystore passwords.
2. Run the sniffer feed on the server, in daemon mode.
- READ THIS to see how to grab the sniffer files and run them locally rather than via Java Webstart.
- Configure the sniffer by creating a "pro2be.properties" file in the ".deepnode" directory in the home directory of the user which will run the sniffer process. Here's an example:
listenport=4020
snortcommand=
max_packets_cached=5000
"listenport=4020" will cause the sniffer to listen on port 4020.
"snortcommand=" will cause the sniffer to not run snort; put your snort command in here, making sure to include "-A console", to have the sniffer run a snort process in order to monitor alerts.
"max_packets_cached=5000" will cause the sniffer to cache only the most recent 5000 packets it has seen. The sniffer caches packets so that when a user hovers over the packet header in the console, the sniffer can send the actual packet contents for visualization.
- Put the hubserver.jks keystore file into the .deepnode directory.
- Run the sniffer with the commandline parameter "daemon" to prevent it from opening a dialog window, and to make it listen for connections from clients; with this option, the sniffer will start monitoring as soon as it is run. The command to run the sniffer will be something like this:
sudo java -cp 3sh3ll_probe.jar:commons-codec-1.9.jar com.threeshell.Pro2be daemon
(you have to use sudo to be allowed to open the interfaces in promiscuous mode)
3. Launch the Hub Feed.
- Configure it with the address of the server you are monitoring as "hub address", and the listen port you gave the sniffer, as "hub port".
- Place the hubclient.jks keystore file into the .deepnode directory within your home directory.
- Click the MONITOR button.
4. Launch the Console and the hub feed will connect to it, connect to the sniffer, and begin streaming data.
Example commands:
mkdir dnprobe
cd dnprobe
wget http://deepnode.us/apps/lib/3sh3ll_probe.jar
wget http://deepnode.us/apps/lib/commons-codec-1.9.jar
sudo mkdir /root/.deepnode
echo "snortcommand=" > pro2be.properties
sudo mv pro2be.properties /root/.deepnode/.
sudo java -cp 3sh3ll_probe.jar:commons-codec-1.9.jar com.threeshell.Pro2be daemon
(default listen port is 4020)
keytool -genkey -alias server -keyalg RSA -keystore hubserver.jks -storepass deepnode
keytool -genkey -alias client -keyalg RSA -keystore hubclient.jks
keytool -export -file server.cert -keystore hubserver.jks -storepass deepnode -alias server
keytool -export -file client.cert -keystore hubclient.jks -alias client
keytool -import -file client.cert -keystore hubserver.jks -storepass deepnode -alias client
keytool -import -file server.cert -keystore hubclient.jks -alias server
You will be prompted for a password for the client keystore. The password for the server keystore must be "deepnode". Make the key passwords the same as the keystore passwords.
2. Run the sniffer feed on the server, in daemon mode.
- READ THIS to see how to grab the sniffer files and run them locally rather than via Java Webstart.
- Configure the sniffer by creating a "pro2be.properties" file in the ".deepnode" directory in the home directory of the user which will run the sniffer process. Here's an example:
listenport=4020
snortcommand=
max_packets_cached=5000
"listenport=4020" will cause the sniffer to listen on port 4020.
"snortcommand=" will cause the sniffer to not run snort; put your snort command in here, making sure to include "-A console", to have the sniffer run a snort process in order to monitor alerts.
"max_packets_cached=5000" will cause the sniffer to cache only the most recent 5000 packets it has seen. The sniffer caches packets so that when a user hovers over the packet header in the console, the sniffer can send the actual packet contents for visualization.
- Put the hubserver.jks keystore file into the .deepnode directory.
- Run the sniffer with the commandline parameter "daemon" to prevent it from opening a dialog window, and to make it listen for connections from clients; with this option, the sniffer will start monitoring as soon as it is run. The command to run the sniffer will be something like this:
sudo java -cp 3sh3ll_probe.jar:commons-codec-1.9.jar com.threeshell.Pro2be daemon
(you have to use sudo to be allowed to open the interfaces in promiscuous mode)
3. Launch the Hub Feed.
- Configure it with the address of the server you are monitoring as "hub address", and the listen port you gave the sniffer, as "hub port".
- Place the hubclient.jks keystore file into the .deepnode directory within your home directory.
- Click the MONITOR button.
4. Launch the Console and the hub feed will connect to it, connect to the sniffer, and begin streaming data.
Example commands:
mkdir dnprobe
cd dnprobe
wget http://deepnode.us/apps/lib/3sh3ll_probe.jar
wget http://deepnode.us/apps/lib/commons-codec-1.9.jar
sudo mkdir /root/.deepnode
echo "snortcommand=" > pro2be.properties
sudo mv pro2be.properties /root/.deepnode/.
sudo java -cp 3sh3ll_probe.jar:commons-codec-1.9.jar com.threeshell.Pro2be daemon
(default listen port is 4020)